Be Aware ! New Android malware is pretended to be System update
Last week research from the Zimperium zLabs researchers disclosed spyware that pretends to be a system update, only to take total control of the smartphone after being installed.
On this malware attack, Shridhar Mittal (Zimperium CEO) said the malware was likely part of a targeted attack. He also says that “It’s easily the most sophisticated we’ve seen,” I think a lot of time and effort was spent on creating this app. We believe that there are other apps out there like this, and we are trying our very best to find them as soon as possible.”
How does malware work?
This is the malware that comes along with an app called ‘system update ’ that has to be installed outside of the google play store. The spyware creates a notification when the mobile screen is off. The user received a command using the firebase messaging services, “The ‘Searching update is not a legitimate notification from the operating system, but the spyware”.
Two options are mentioned to update the device the information exists as “update” and “refreshAllData”. “update,” option collected device information and send it to C&C, whereas “refreshAllData,” generated and exfiltrated a new firebase token.
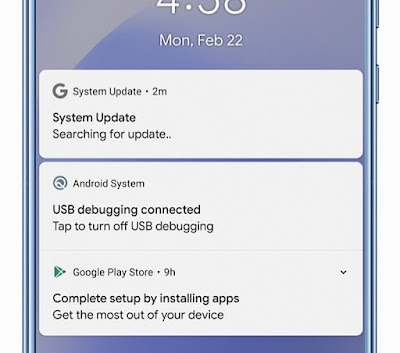 |
| A screenshot of the malware masquerading as a system update running on an Android phone. The malware can take full control of an affected device. (Image: Zimperium) |
This spyware performs a wide range of malicious activities to spy on the users while posing as a “system update” application.
What can malware steals?
The application poses a threat to android devices by functioning as RAT (Remote access Trojan) that receives and executes commands to collect and exfiltrate a wide range of data and perform a wide range of malicious actions, as follows
- Massages
- Brower’s history, bookmark, searches
- Document
- Clipboard data
- Record calls
- Microphone
- Take photos using a phone's camera
- Location
- Call log
- SMS log
- Phone contacts
The malware can also organize the collected data into some folder inside its private storage, and it also can wipe out any trace of malicious activity by deleting the zip files as soon as it receives a success message from the C2 server post exfiltration. It also reduces bandwidth consumption by uploading thumbnails.
Android devices always warn users not to install any other app from outside of the app store.
CEO of Zimperium zLabs Mittal confirmed that the malicious app was never installed on google play. So there is no worry if you are only downloading the apps from the google play store and losing control of your phone. It also looks like a targeted attack, considering how thoroughly the malware scans a device.
How to avoid malware attacks?
- The best practices to avoid the malware attack is to avoid downloading the app outside the google play store
- Always keep up to date your device with verified Google security patches
- Avoid downloading the app from other sites or others play store
Read also: Your smart device may not be safe, remains unprotected to hacking









Post a Comment